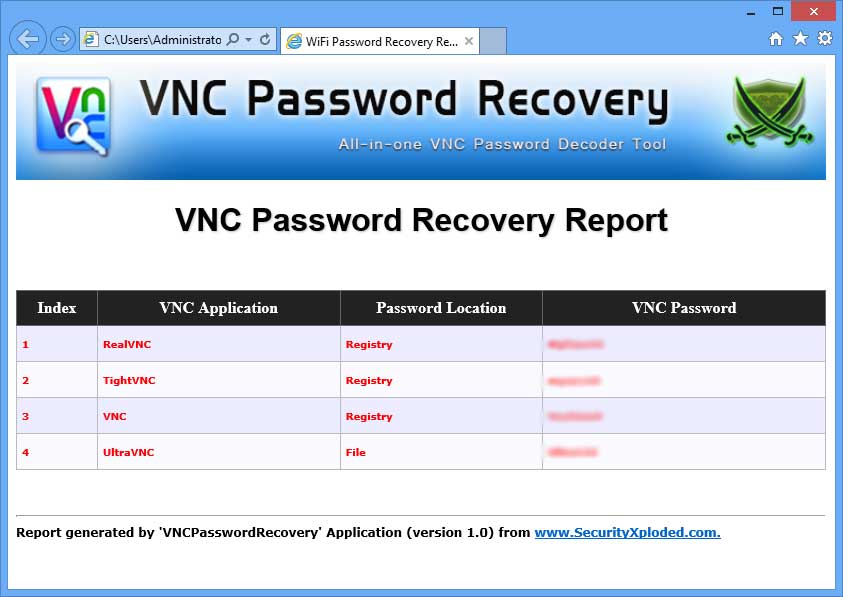
Crack Or Decrypt Vnc Server Encrypted Password
Aug 24, 2000 - Loki, These passwords are stored in an encrypted form in the registry. Use VNC on workstations - to support user problems and on servers - for remote admin. VNC passwords - Tool required There's a tool called vnccrack.
Welcome back, my fledgling hackers!
There's an evil dictator hellbent on destroying the world, and in one of our last hacks, we successfully compromised his computer and saved the world from nuclear annihilation. Then, we covered our tracks so no one would know what we did, and developed a hack to capture screenshots of his computer periodically so we could track of what he was up to next.
With this new hack, we'll capture the passwords from the maniacal dictator's computer so that we can access his PC through his account— or anyone else's account on his computer, including the most important account—the system administrator's.
I don't remember my password for one of my servers. I have a working connection saved and want to get the password from it.
From Remmina faq:
Q: How are my passwords stored? Are they secure?
A: They are encrypted using 3DES with a 256bit randomly generated key. You should keep your key secure.
So where do I get the key and where would the passwords be stored?
EDIT:Ok found that they are just in your users home folder under .remmina.both the private key are in base64 and i can't seem to get the password right when decrypting...
Decrypt Cisco Encrypted Password
6 Answers
I was able to use the Go solution by @michaelcochez to decrypt it with Python:
I found the key in a file called ~/.remmina/remmina.prefs and the encrypted passwords are in ~/.remmina/nnnnnnnnnnn.remmina.
I wrote a code (in Go) which can be used for decryption:
The code can be run online, but then you are trusting golang.org.
They are stored in Gnome-Keyring.
Dash->type 'keys'->Passwords&Keys.
In newer versions of seahorse (a.k.a. 'Passwords and Keys') one has to select 'View' -> 'Show any' to see the keys. Search for 'remmina'.
I made a script that automatically decrypt your password files. The most recent version is at https://github.com/peppelinux/remmina_password_exposer.
I created a perl script to decode remmina passwords. It extract your key and decode all your saved passwords (locally).
https://github.com/lepe/scripts/blob/master/decode_remmina.pl (check for updated version)
How to install rapelay mods. You will need to install these packages (for example, using cpan <PACKAGE>): Crypt::CBC, Crypt::DES_EDE3, MIME::Base64, File::Slurp
Sample output:
(Name, host, user, password: tab separated)

I needed to do the reverse and encrypt passwords for Remmina using a Python script. In case anyone needs it here's the code: